
Introduction
In response to the severe fallouts of recent cyber breaches, the federal government issued an Executive Order (EO) 14028, “Improving the Nation’s Cybersecurity.” Among other policy mandates, the EO recommends Zero Trust Architecture (ZTA) as the desired model for security.
In January 2022, the executive office of the President issued a memorandum M-22-09 “Moving the U.S. Government Toward Zero Trust Cybersecurity Principles” that reinforces the Zero Trust imperative in EO 14028. Setting forth a strategy for ZTA, this memo requires federal agencies to launch a Zero Trust implementation strategy before April 2022 to achieve Zero Trust security goals by the end of the fiscal year 2024.
ZTA represents a set of system design principles and a coordinated cybersecurity and system management strategy. It eliminates implicit trust in any entity (user, device, etc.) that requests access to enterprise data and resources.
Today, users access company resources from anywhere, using any device. There is an ever-increasing reliance on SaaS applications and other cloud services. Zero Trust creates a transition from a geographical-centric model to a more data centered approach for more granual security controls between users, systems, data, and assets in such dynamic threat environments that keep changing over time. These factors make the transition to ZTA non-trivial.
Achieving Zero Trust is a progressive journey that requires a proper understanding of the principles and a systematic approach to implementing appropriate cybersecurity controls.
What Zero Trust Is and Isn’t
The National Institute of Standards and Technology (NIST) Special Publication (SP) 800-207 provides the following operative definition of Zero Trust and ZTA:
Zero Trust provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.
ZTA is an enterprise’s cybersecurity plan that uses zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a ZTA plan.
In summary:
- Zero Trust is a set of security design principles
- ZTA is a set of guidelines to help organizations in their cybersecurity maturity journey
- No single product or solution can provide Zero Trust
- Zero Trust is not a destination in itself
Seven Key Tenets of the Zero Trust Architecture
The scope of Zero Trust is not limited to removing implicit Trust associated with enterprise trust boundaries. To clearly define what Zero Trust includes, NIST SP 800-207 defines the seven basic tenets of Zero Trust:
-
- Resources encompass all sources of data and computing services. The enterprise infrastructure includes various devices. All devices and services, regardless of their scope and ownership that access enterprise networks, are included as resources.
- All communication is secured regardless of network location. Trust should not be granted based on whether the requesting entity is inside or outside the corporate trust boundary. Access requests from assets located on enterprise-owned network infrastructure must meet the same security requirements as access requests and communication from the non-enterprise-owned network.
Zero Trust provides security design principles to enable organizations progress in their cybersecurity maturity journey.
- Access to individual enterprise resources is granted on a per-session basis. For every new session, access is granted to the requesting devices after authentication and authorization, even if Trust was established previously for the same device “sometime recently.” Access is granted on the least privileged basis needed to complete the task and for every access request.
- Access to resources is determined by dynamic policy—including the observable state of client identity, application/service, and the requesting asset—and may include other behavioral and environmental attributes. Access to a resource is not a static concept. Missing security patches, a suspicious login, and other factors may still block access even if the requesting client is authorized to view a particular resource.
- The enterprise measures and monitors the security posture and integrity of all assets. The security state of assets can vary over time. The security posture of the asset must be validated at the time of evaluating a resource request. An enterprise implementing a ZTA should establish a continuous diagnostics and mitigation (CDM) or similar system to monitor the security state of devices and applications and should apply patches/fixes as needed.
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed. This is a constant cycle of obtaining access, scanning and assessing threats, adapting, and continually reevaluating Trust in ongoing communication.
- The organization collects adequate information about the current position of assets, network infrastructure, and communications and leverages it to improve its security posture. Organizations should use the information collected from initial zero trust deployments to ease the transition and improve their security posture.
These tenets are technology agnostic and meant to guide your organization’s Zero Trust journey.
Five Pillars of the CISA Zero Trust Maturity Model
Zero Trust cannot be achieved overnight. To help organizations make the right decisions, Cybersecurity and Infrastructure Security Agency (CISA) developed a Zero Trust Maturity Model to assist agencies in implementing Zero Trust architectures. The maturity model complements the Office of Management and Budget’s (OMB) Zero Trust Strategy, that provides agencies with a roadmap and resources for achieving an optimal Zero Trust environment.
The Zero Trust Maturity Model is one of many paths to achieve Zero Trust and defines five distinct pillars, namely, Identity, Device, Network, Application Workload, and Data (Figure 1). Each pillar includes three ZTA capabilities:
- Visibility and analytics is the capability to monitor and analyze user activity and user behaivior.
- Automation and orchestration of identity and credentials, user profiling, access controls, etc.
- Governance is about enforcing access policies and regular audits of identities and permissions.
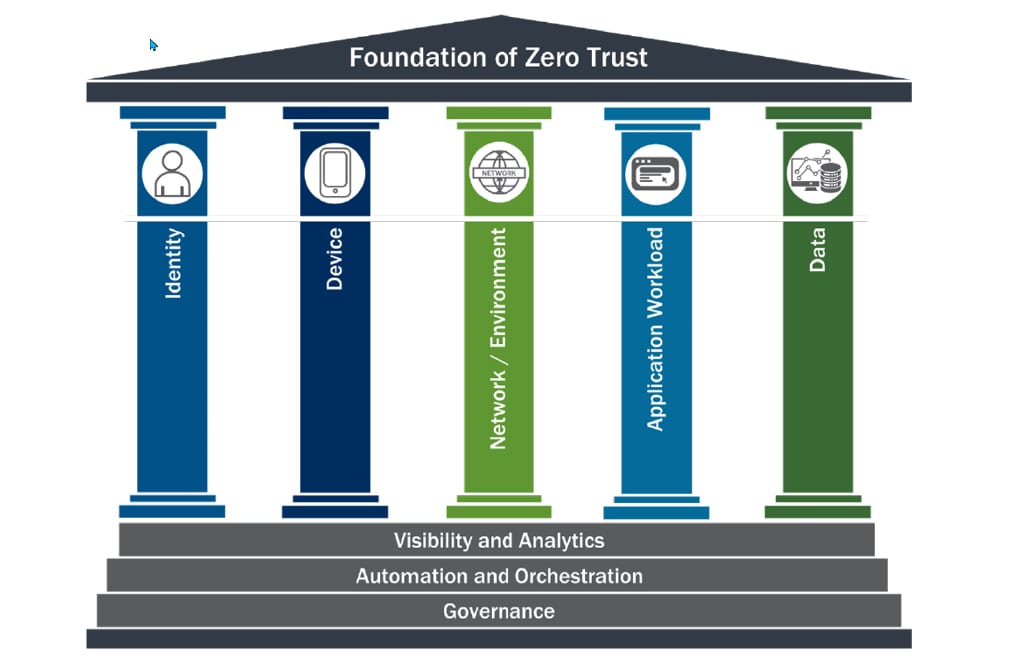
Figure 1: Foundation of Zero Trust (Source CISA)
Zero Trust Maturity Model is one of many paths to support the transition to zero trust.
Pillar #1 Identity
Identity refers to an attribute or set of attributes that uniquely describe an agency user or entity. Agencies should ensure and enforce that the right users and entities have the right access to the right resources at the right time.
Pillar #2 Device
A device refers to any hardware asset connecting to a network, including Internet of Things (IoT) devices, mobile phones, laptops, servers, and others. A device may be agency-owned or bring-your-own-device (BYOD). Agencies should inventory devices, secure all agency devices, and prevent unauthorized devices from accessing resources.
Pillar #3 Network and/or Environment
A network denotes an open communications medium, including an agency’s internal and wireless networks, as well as, the Internet used to transport messages. Agencies should segment and control networks and manage internal and external data flows.
Pillar #4 Application Workload
Applications and workloads include agency systems, computer programs, and services that execute on-prem and in the cloud. Agencies must securely manage the application layer and containers and provide secure application delivery.
Pillar #5 Data
Agency data should be secured on devices, applications, and networks. Agencies should inventory, categorize, and label data, protect data at rest and in transit, and deploy mechanisms for detection data exfiltration.
The model mentions three stages of the maturity gradient, namely, traditional, advanced, and optimal, with increasing protection and complexity of adoption.
The Traditional stage involves manual configurations, assignment of attributes, static security policies, manually managing dependencies on external systems, manual incident response, etc.
The Advanced stage refers to some centralized visibility, centralized identity control, cross-pillar coordination, some least-privilege changes based on posture assessments, etc.
In the Optimal stage the Zero Trust capabilities are fully automations and least-priviledge based assignments to assets amd resources is dynamic.
As organizations transition to optimal, their solutions are more reliable and fully integrate across the pillars.
The Federal Government’s memorandum on Zero Trust strategy requires agencies to achieve specific Zero Trust security goals. The memo defines actionsable steps to achieve these strategic security goals, which aligns with the five pillars of CISA’s Zero Trust Maturity Model and the three thremes that cut across these pillars – Visibility and Analytics, Automation and Orchestration, and Governance.
Conclusion
Zero Trust is essential to mitigate modern threats. Enforcing access controls that are as fine-tuned as possible, Zero Trust prevents unauthorized access to data and services. Zero Trust is an arduous journey. Achieving Zero Trust for your organization calls for a systematic strategy and game plan that align with the tenets defined by NIST SP 800-207. The five pillars of the Zero Trust Maturity Model provide the guidance you need in your Zero Trust journey.
Recent Posts:

Advanced Cloud Protection via Containerization

An ultimate guide to Docker and Kubernetes

An Ultimate Guide to Managing Cloud Security Posture across Environments

The Truth behind Cloud Security and Shared Responsibility Models

Zero Trust is not a destination; it’s a complex journey
