
Introduction
Since 2020, high-profile cyber incidents have made frequent headlines. The massive malware attack targeting SolarWinds’ “software supply chain” impacted 33,000 SolarWinds customers, which included the private sector and the United States federal agencies. Within months, the fallouts of the ransomware attacks on Colonial pipeline and JBS rippled across the U.S. supply chain. In March 2021, state-sponsored threat groups successfully compromised the on-premises version of the Microsoft exchange server affecting reportedly 30,000 private and federal organizations all over the U.S.
Considering the growing trend of organized cyber incidents and their impact, the federal administration declared cyber breaches a threat to national security, economic growth, and public health and safety. In May 2021, President Biden signed Executive Order 14028, “Improving the Nation’s Cybersecurity.” The primary goal of this Executive Order (EO) is to
“Support our nation’s cybersecurity and protect the critical infrastructure and Federal Government networks underlying our nation’s economy and way of life.”
The order lists a series of drastic cybersecurity initiatives, most notably, the Zero Trust Architecture (ZTA).
On January 26, 2022, the executive office of the President issued a memorandum M-22-09 “Moving the U.S. Government Toward Zero Trust Cybersecurity Principles.” This memo reinforces the imperative of ZTA in EO 14028. Setting forth a strategy for ZTA, the memo requires federal agencies to meet specific cybersecurity standards and objectives to achieve Zero Trust security goals by the end of the fiscal year 2024.
Security imperatives set by the Cyber Executive Order
Cybersecurity is no longer optional. The Executive Order (EO) underscores cybersecurity as a critical pillar of national security. It recognizes malicious cyber campaigns as persistent and increasingly sophisticated threats to the public and private sectors. The EO defines the pivotal role of the Federal Government to identify, deter, prevent, detect, assess and respond to threats and threat actors as essential to national and economic security. It recognizes that this is achievable through federal agencies partnering with private enterprises. Thus the EO brings to its fold all U.S organizations:
“The private sector must adapt to the continuously changing threat environment, ensure its products are built and operate securely, and partner with the Federal Government to foster a more secure cyberspace.”
The scope of the protection involves all information systems, irrespective of those being cloud-based, on-premises, or hybrid. It includes both IT (Information Technology) systems that process data and the OT (Operational Technology) systems that run the vital machinery ensuring our safety.
As a crucial security measure, the EO recommends agencies adopt Zero Trust and adjust their network architectures accordingly. The EO defines Zero Trust as follows:
The term “Zero Trust Architecture” means a security model, a set of system design principles, and coordinated cybersecurity and system management strategy based on an acknowledgment that threats exist both inside and outside traditional network boundaries.
The Zero Trust security model eliminates implicit trust in any one element, node, or service |
The Zero Trust security model eliminates implicit trust in any one element, node, or service and instead requires continuous verification of the operational picture via real-time information from multiple sources to determine access and other system responses. In essence, a Zero Trust Architecture allows users full access but only to the bare minimum they need to perform their jobs.”
The memo M-22-09 translates the EO recommendations into actionable steps for implementing Zero Trust. It requires agencies to rise above trusted network centric perimeter-based security controls to Zero Trust where nothing is trusted. This strategy emphasizes the need for stronger enterprise identity and access control, for example, by requiring agencies to use phishing-resistant multi-factor authentication (MFA). The memo also a sets the timeline for implementing zero trust strategy:
- Within 30 days from the issuance of the memo agencies must designate a Zero Trust strategy implementation lead for their organization.
- Agencies must submit a Zero Trust implementation plan and budget to federal authorities with 60 days from the issue date of the memorandum
What is Zero Trust – NIST 800-207
The Zero Trust Architecture (ZTA) is a security paradigm where breaches are considered inevitable or have likely already occurred. As the name suggests, no assets are trusted – “Never Trust; Always Verify” is the core principle of Zero Trust. It eliminates implicit trust that assumes every entity (device, users, etc.) within the corporate trust boundary as secure.
Zero Trust requires you to continuously verify the user and device identity and security state and limit access to only what is needed to perform the task. Comprehensive security monitoring, granular risk-based access control, and system security automation are integral to the ZTA. This allows protecting data in real-time in dynamic threat environments. ZTA is a data-centric security model where least-privileged access is applied for every access decision. The answers to who, what, when, where, and how are critical for appropriately allowing or denying access to resources.
The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST), responsible for promoting the U.S. economy and public welfare with technical guidance, issued a special publication (SP) 800-207 on Zero Trust. SP 800-207 highlights four main aspects of the Zero Trust security paradigm:
- Replace “implicit trust zones” with the explicit establishment of trust. Implicit trust zones are specific areas such as the corporate network where all entities (devices and users) are implicitly trusted.
- Implement security controls with the assumption that the network is already compromised.
- Prevent unauthorized access to data and services and make access control enforcement as granular as possible. Only authorized and approved subjects (combination of user, application, service, and device) can access the data and resources to the exclusion of all other subjects (i.e., attackers).
- Make access rules as granular as possible to enforce the least privileges needed to perform the action in the request.
Why Enterprises need Zero Trust
Cyberattacks are no longer limited to mere DDoS attacks. Advanced persistent threats are now highly complex and organized with national, societal, physical, and financial repercussions. In 2021, the average cost of a data breach reported by the Ponemon Institute rose to an all-time high of USD 4.24 million.
The average cost of a data breach reported by the Ponemon Institute rose to an all-time high of USD 4.24 million in 2021.
Traditional security architectures relied on corporate trust boundary, aka., the network perimeter. In a cloud-oriented ecosystem, the idea of a corporate trust boundary sounds quaint. Today, applications and users are no longer confined to corporate locations. Users access applications in the public cloud, as SaaS apps, in private clouds (both hosted and non-hosted), in addition to traditional on-premise datacenters. When your customers and workforce frequently access apps and workloads in the cloud from non-enterprise locations, the idea of enterprise-centric trust boundary loses relevance. Consequently, access control solutions like firewalls fail to keep up with new attack vectors targeting user credentials and device vulnerabilities.
The Zero Trust security framework eliminates implicit, transitive trust that underpins the perimeter-centric paradigm: everything inside the corporate perimeter is trustworthy. In a “perimeter-less” world, Zero Trust never takes trust for granted. Zero Trust begins with robust authentication and granular access control. It verifies users’ identities and the security of transactions irrespective of location. This prevents attackers at the point of entry: when they request access.
Implement your Zero Trust Initiatives with CIS Controls
The latest version (version 8) of Center for Internet Security (CIS) controls supports a Zero Trust architecture in addition to recommendations for built-in security, pervasive encryption, allow-list functionality, and supply chain security risk reduction that the EO calls out. The CIS Controls v8 breaks down the Zero Trust journey into achievable steps while reducing risks based on current threats. Your organization can make progress in the Zero Trust journey while being assured that the steps taken are prioritized in a meaningful way. The following illustration maps Zero Trust with the CIS Controls.
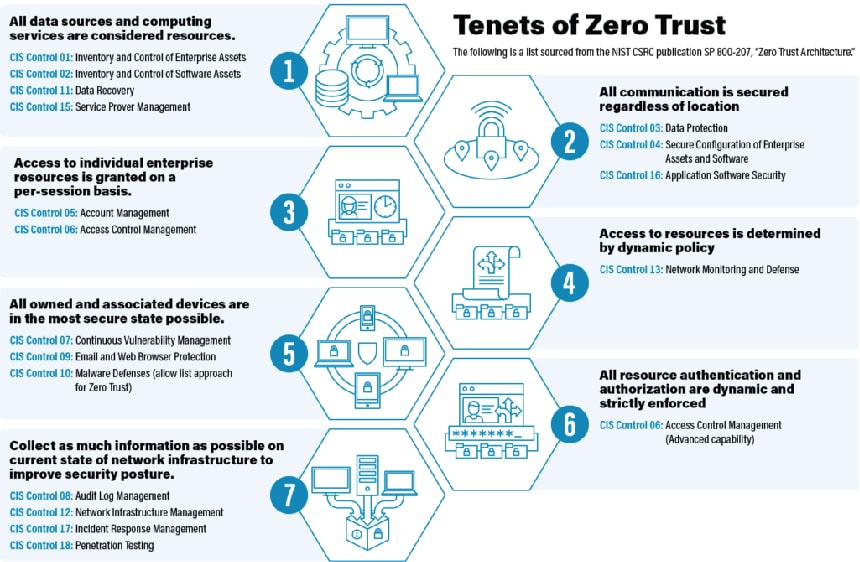
Conclusion
The Executive Order explicitly established cybersecurity as an undeniable necessity for national security, economy, and wellbeing. Robust cybersecurity measures are no longer optional. The order recognizes the critical role of the Zero Trust security model in protecting enterprises and the nation’s critical infrastructure from highly organized attacks in dynamic threat environments. Zero Trust eliminates implicit trust by requiring granular access verification at every access request, which is the key to preventing malicious actors and devices from gaining access to your resources. Federal agencies like CISA, NIST, and CIS are publishing additional guidance for implementing Zero Trust. We can make your Zero Trust journey seamless.
Contact our team of experts to learn more.
Recent Posts:

Advanced Cloud Protection via Containerization

An ultimate guide to Docker and Kubernetes

An Ultimate Guide to Managing Cloud Security Posture across Environments

The Truth behind Cloud Security and Shared Responsibility Models

Zero Trust is not a destination; it’s a complex journey
