
A recent survey from Samsung shows the importance of implementing cybersecurity measures across an extended network. The survey points out that 64% of federal government IT and cybersecurity professionals see endpoint security breach prevention as a priority.
The Office of the Director of National Intelligence (ODNI) publishes an annual review that details the security threats facing the United States. In the report “2019 Worldwide Threat Assessment,” cyber-threats are identified as one of the top strategic issues in the U.S. The 2020 DHS Homeland Threat Assessment report reiterates this finding.
Cybersecurity continues to plague government entities, including the DoD (Department of Defense) and its vendor ecosystem, made up of around 300,000 suppliers.
The Cybersecurity Maturity Model Certification (CMMC) program came into force in October 2020. The CMMC is a framework to ensure DoD suppliers work to an optimized security posture. To demonstrate compliance with the CMMC, DoD suppliers must obtain third-party certification from a Third-Party Assessment Organization (C3PAO).
This compliance involves meeting the criteria set out in five core CMMC levels.
Levels 1-5 of the CMMC
The CMMC is designed to allow DoD suppliers to demonstrate the ability to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
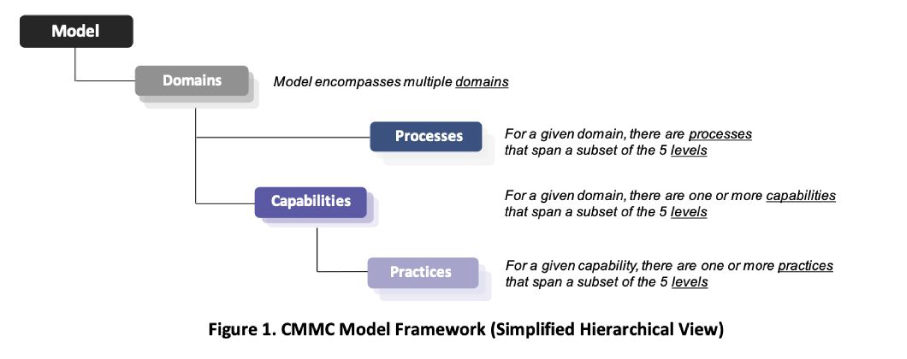
The CMMC is an ecosystem in its own right. Drawing from existing cybersecurity standards, from the likes of NIST SP 800-171 and DFARS (Defense Federal Acquisition Regulation Supplement) clause 252.204-7012, the CMMC sets out a framework model. This framework creates a series of best practices and guidelines across five increasing maturity levels.
This CMMC Framework Model comprises:
- The Model
- 17 capability domains
- 43 capabilities
- 171 practices across five levels to measure technical capabilities
- 5 processes across five levels to measure process maturity
- 43 capabilities
- 17 capability domains
The whole ties together using five ‘levels of maturity.’
Source: CMMC Version 1.02
CMMC Level 1
Process: Performed
Documentation in level 1 is a “could have” as process maturity is not assessed. The practices performed in level 1 are likely to be ad hoc, so documentation is less likely to be associated with these processes.
Practices: Basic safeguarding and cyber hygiene
Level 1 covers cybersecurity basics and is a foundation stone to build on if an organization wishes to increase its CMMC compliance level. DFARS clause 252.204-7012 defines several prerequisites to meet level 1. These include cybersecurity 101 and should be followed by all companies, even those not needing CMMC certification.
For example, one of the safeguards is to “Control information posted or processed on publicly accessible information systems.” The basics also cover physical security, such as physical access, as well as cyber. Perhaps one of the most intrinsic and far-reaching of these basics is to “Monitor, control, and protect organizational communications.” In a world where email is the vector of choice by cybercriminals, this basic requirement is one for everyone to note.
Level 1 has to meet 17 practices for compliance.
CMMC Level 2
Process: Documented
Documentation is a ‘must-have’ at this level. Level 2 expects that your organization has definite documentation on policies and practices to demonstrate CMMC compliance. The documentation enumerates the maturity of your cybersecurity posture.
Practices: Intermediate Cyber Hygiene
Level 2 is a half-way house between levels 1 and 3 in terms of meeting security requirements. Whereas level 1 was more about the protection of FCI, this level focuses attention on protecting CUI. Some of the requirements in NIST SP 800-171 set the bar for CMMC level 2. Examples of additional controls include “limit unsuccessful logon attempts” and “employ the principle of least privilege…”
Level 2 adds 55 new practices to level 1 to meet compliance.
CMMC Level 3
Process: Managed
At level 3. an organization is expected to organize, establish, report, and maintain processes. Level 3 is about planning and demonstrating the management of activities for practice implementation.
Practices: Good cyber hygiene
Level 3 is where things become more in-depth in terms of cybersecurity measures. This level builds on levels 1 and 2 and builds more robust defenses in the protection of CUI. All of the security practices outlined in NIST SP 800-171 are required for this level. Included are practices to mitigate threats. The DFARS clause 252.204-7012 continues to apply and goes beyond NIST SP 800-171 to include incident reporting. Level 3 includes requirements such as the use of MFA.
Level 3 total practices rise to 130, an additional 58 including level 2 practices.
CMMC Level 4
Process: Reviewed
At level 4, an organization is expected to review and measure the effectiveness of any cybersecurity measures they use.
Practices: Proactive
A government contractor at level 4 can demonstrate proactive prevention of CUI exposure from threats such as Advanced Persistent Threats (APTs). To achieve level 4, an organization needs to enhance security requirements from NIST SP 800-171B. Level 4 is about being proactive, using cybersecurity best practice measures that offer advanced detection and response capability.
Level 4 total practices rise to 156.
CMMC Level 5
Process: Optimizing
An organization that achieves level 5 demonstrates an advanced cybersecurity posture. At level 5, you must provide evidence that cybersecurity process implementation is both standard and optimal.
Practices: Advanced progressive
At level 5, an organization has a raft of cybersecurity practices in place. Level 5 measures provide proactive protection against CUI attacks. This level is about putting advanced cybersecurity measures in place and making sure they are optimized for the current cybersecurity threat landscape. Proactive systems that can detect and respond to APTs and other advanced threat mitigation techniques are associated with this CMMC level achievement.
Level 5 takes the total practice number to 171.
Forging Ahead with the CMMC Levels
To work with the DoD as a contractor, an organization must meet the requirements of one of the five CMMC levels. The type of contractor and the type of contract determine the required level. One good thing about the CMMC is that the five levels are cumulative, so each builds upon the previous. Once you have the relevant security practices in place for one level, you can more easily move to the next level.
Whatever level your organization needs to meet, certification must be done using a Third-Party Assessment Organization (C3PAO). Having a third-party oversee your CMMC certification means you have an experienced hand to take you through the process. Getting your level practices in place will allow you to work with the government and ensure that you conform to security best practices.
Recent Posts:

Advanced Cloud Protection via Containerization

An ultimate guide to Docker and Kubernetes

An Ultimate Guide to Managing Cloud Security Posture across Environments

The Truth behind Cloud Security and Shared Responsibility Models

Zero Trust is not a destination; it’s a complex journey
